
How exposed are you?
On Thursday, September 15th, 2022, Uber was hacked by an 18-year-old using social engineering, followed by a privilege escalation attack on an internal network. News of the attack comes as Uber’s former security chief stands trial over a 2016 breach in which the records of 57 million users and drivers were stolen”.
As you have read about the incident, you have no doubt turned to your IT guys and asked: “Can this happen to us?” – to which they probably responded in a manner that set your mind at ease… But are you safe?
The truth is no one is safe. So there, you have it. – No, Really, you are not… I’m not just making a shock statement for effect!
Cyber Security is not a state you achieve. It is fluid and constantly changing. What is Next-Gen AI today is old news tomorrow. Earlier this month, CBS reported that according to the FBI, Americans alone had lost nearly seven (7) billion dollars to cybercrime in 2021. That’s a lot of money. Just pause and think how much money that is. Cybercrime is BIG business!
Cybersecurity is all about layers. It’s about People, Processes and Policies, and just like you, I bet that on September 14th, Uber thought that they had that waxed! It’s always ok until it’s not, isn’t it? In the aftermath of the attack, it looks like although Uber’s Processes and Policies failed, it was ultimately the human component (the People) in the equation that proved to be the weakest link in their cyber defense.
The following schematic is my understanding of what happened:
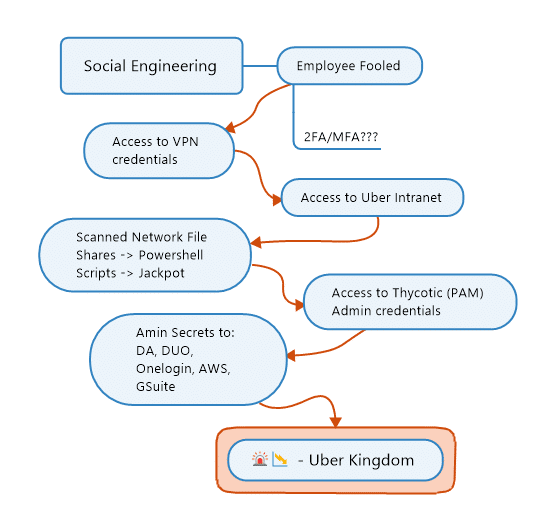
Lessons for Business Owners:
Cybersecurity is not just the responsibility of your IT provider. In fact, unless your IT provider explicitly includes Cyber Security Insurance in your fee, you can safely assume that you need to ensure your own insurance thereof. It is your responsibility to ensure that (1) you have a program in place for Cyber Security Awareness Training and (2) to ensure that your company has a policy where no user (including yourself) and your IT people ever use admin accounts for day-to-day use.
The details of the attack are still sketchy, but I highly doubt the initial compromised user was an ordinary user. An admin account must have been involved early on, and it is a mystery how the 2FA (2 Factor Authentication) or MFA (Multi-Factor Authentication) was bypassed.
If you want to hear more about our Cyber Security Awareness Training, or if you want to talk to us about designing cybersecurity layers for your company, reach out today for an obligation-free discussion or assessment.





Related Posts